In October 2023, a significant software security vulnerability was discovered that impacts Microsoft Teams. The vulnerability, designated as CVE-2023-4863, affects not only Microsoft Teams but also Microsoft Edge, Skype for Desktop, and WebP Image Extensions.
Although software updates have been released for Microsoft Teams, Microsoft Defender continues to flag multiple devices as vulnerable. The persistence of this vulnerability is due to the Machine-wide Installer, which installs Teams for all profiles, while deployed updates only update the Teams.exe file for the logged-in user.
While Microsoft does not provide direct remediation for this specific issue, there are steps you can take to address it. Although manual remediation via scripting may not be ideal, a script released on GitHub by Lee Vilenski has proven to be very successful.

We have modified Vilenski’s script to meet our requirements and deployment methods, as shown below. The original script can be found here.
Script
# Define minimum acceptable version (replace with your desired version)
$minVersion = “1.7.00.8651”
############### Do Not Edit Below This Line #################################
###Finding SIDs for loop
# Regex pattern for SIDs
$PatternSID = ‘S-1-5-21-\d+-\d+\-\d+\-\d+$’
# Get Username, SID, and location of ntuser.dat for all users
$ProfileList = gp ‘HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\*’ | Where-Object {$_.PSChildName -match $PatternSID} |
Select @{name=”SID”;expression={$_.PSChildName}},
@{name=”UserHive”;expression={“$($_.ProfileImagePath)\ntuser.dat”}},
@{name=”Username”;expression={$_.ProfileImagePath -replace ‘^(.*[\\\/])’, ”}}
# Get all user SIDs found in HKEY_USERS (ntuder.dat files that are loaded)
$LoadedHives = gci Registry::HKEY_USERS | ? {$_.PSChildname -match $PatternSID} | Select @{name=”SID”;expression={$_.PSChildName}}
# Get all users that are not currently logged
$UnloadedHives = Compare-Object $ProfileList.SID $LoadedHives.SID | Select @{name=”SID”;expression={$_.InputObject}}, UserHive, Username
# Loop through each profile on the machine
Foreach ($item in $ProfileList) {
# Load User ntuser.dat if it’s not already loaded
IF ($item.SID -in $UnloadedHives.SID) {
reg load HKU\$($Item.SID) $($Item.UserHive) | Out-Null
}
#####################################################################
# Check and potentially remove outdated Teams versions
# Get Teams uninstall keys for the user
$teamsUninstallKeys = Get-ItemProperty registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\Teams*
if ($teamsUninstallKeys) {
foreach ($teamsKey in $teamsUninstallKeys) {
# Check DisplayVersion and remove key if outdated (with confirmation)
$displayVersion = $teamsKey.DisplayVersion
if ($displayVersion -lt $minVersion) {
$uninstallString = “C:\Users\$($item.Username)\appdata\local\microsoft\teams\update”
# Consider error handling for uninstall process (not shown here)
try {
Start-Process -FilePath $uninstallString -ArgumentList “–uninstall” -Wait -Verb RunAsAdministrator
} catch {
}
# Remove the Teams uninstall key (use with caution)
Remove-Item -Path “registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\$($teamsKey.PSName)” -Recurse}
}
} # Unload ntuser.dat
IF ($item.SID -in $UnloadedHives.SID) {
[gc]::Collect()
reg unload HKU\$($item.SID) | Out-Null
}
}
################## Remove Teams where Regkey doesn’t exist #############################
$userProfiles = Get-ChildItem -Path “C:\Users” -Directory -Exclude Default,Public
# Loop through each user profile
foreach ($profile in $userProfiles) {
# Check if Teams executable exists
$teamsPath = Join-Path -Path $profile.FullName -ChildPath “AppData\Local\Microsoft\Teams\current\Teams.exe”
if (Test-Path $teamsPath) {
# Get the installed version
$installedVersion = (Get-ItemProperty $teamsPath).VersionInfo.FileVersion
# Check version – inform about outdated and above versions
if ($installedVersion -lt $minVersion) {
Write-Host “Outdated Teams version found in $($profile): $installedVersion”
# Uninstall Teams (requires admin privileges)
Remove-Item -Path $teamsPath -Recurse -Force -ErrorAction SilentlyContinue
if ($?) {
Write-Host “Uninstalled Teams from $profile successfully.”
} else {
Write-Host “Failed to uninstall Teams from $profile.”
}
} else {
Write-Host “Teams version in $profile ($installedVersion) is above or meets the minimum requirement.”
}
}
}
Please see below steps to implement the remediation script using Microsoft Intune:
- Copy the Script code above into Notepad and save as a PowerShell file (TeamsUpdate.ps1)
- In Microsoft Intune,
- Navigate to the Devices blade,
- Select Scripts and remediations,
- Select the Platform scripts tab
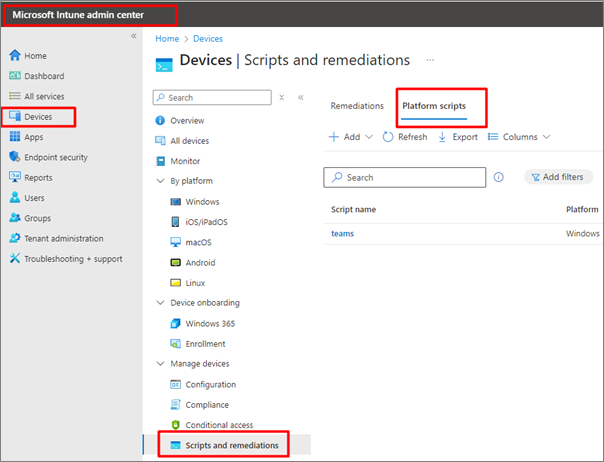
3. Select Add/Create to create a new script, select Windows 10 and later
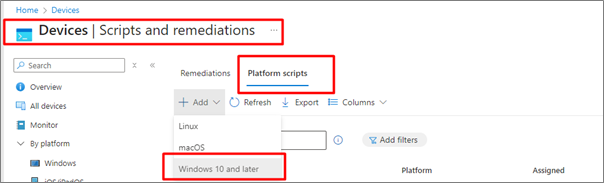
4. Enter Name and Description for script
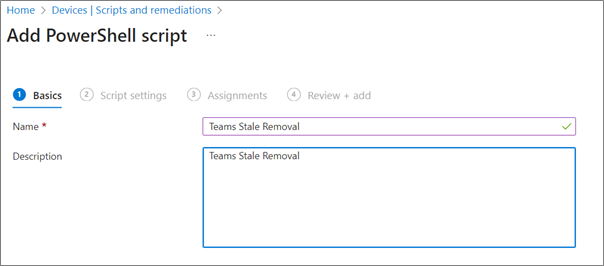
5. Under script settings:
-
- Upload the script
- Set “Run this script using the logged-on credentials” to No
- Set “Enforce script signature check” to No
- Set “Run script in 64bit PowerShell Host” to Yes
6. On next screen, Assign the script to the All devices group
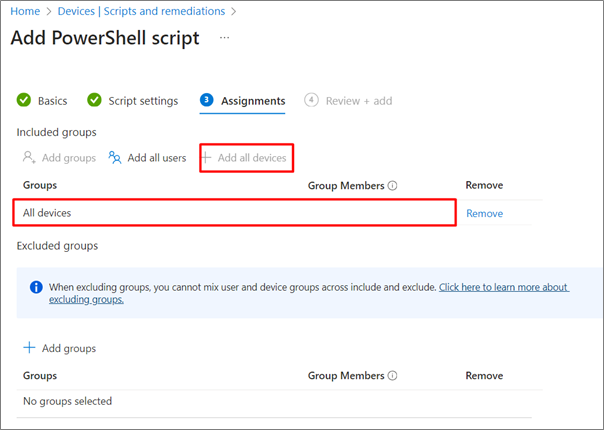
7. Save
By BUI SecOps Principal Technical Consultant, Terryanne du Toit and BUI SecOps Technical Consultant, Danie Miller.
