Zandre Janse van Vuuren identifies five of the most common cyberthreats and shares practical tips to help you defend against them.
By Zandre Janse van Vuuren | Service Delivery Manager: Cyber DFIR, BUI
As our world becomes increasingly interconnected through digital systems, the threat landscape for cyberattacks continues to expand. In 2024, global cybercrime costs soared to an estimated $9.22 trillion, with projections indicating a rise to more than $13 trillion by 2028.
These staggering figures highlight the need for robust security measures. Cyberthreats not only risk sensitive data, but can also disrupt operations and cause significant financial and reputational damage. Let’s take a closer look at five of the most common cyberthreats organisations face today, their potential impact, and actionable steps for mitigation.
Phishing remains one of the most prevalent cyberthreats due to its simplicity and effectiveness. Attackers often exploit human error, leveraging psychological tactics such as urgency, fear, and curiosity to trick people into revealing critical information.
Common phishing techniques include posing as trusted organisations like banks or government agencies, using realistic-looking fake websites to capture login credentials, and embedding malware in email attachments.
The rise of spear phishing (i.e., highly targeted attacks against specific individuals or organisations) has further increased the threat’s sophistication and success rate. Even tech-savvy users can fall victim if vigilance lapses, making continuous awareness and training essential.
Potential impact:
Mitigation:
With the rise of Ransomware-as-a-Service platforms, even attackers with little technical aptitude can deploy sophisticated ransomware campaigns, making this threat more pervasive than ever. These platforms provide pre-packaged ransomware tools, technical support, and even revenue-sharing models, significantly lowering the barrier to entry for cybercriminals.
Compounding the issue is the growing use of double extortion tactics, where attackers encrypt data and threaten to publicly release sensitive information unless the ransom is paid. This evolution has made ransomware one of the most concerning and financially devastating cyberthreats today, affecting organisations of all sizes across industries.
Potential impact:
Mitigation:
While external attacks often dominate headlines, insider threats can be just as damaging and sometimes more difficult to detect. Whether malicious or negligent, insiders already have authorised access to critical systems and data, allowing them to bypass many traditional security measures.
Malicious insiders may act out of financial gain, dissatisfaction, or coercion, while negligent insiders might unintentionally expose sensitive information through careless behaviour or a lack of awareness.
The dual nature of insider threats makes them particularly challenging to manage, underscoring the importance of comprehensive monitoring and regular employee training.
Potential impact:
Mitigation:
Malware attacks are often the first step in larger, multi-stage cyberattacks, serving as a gateway for attackers to establish a foothold in a target’s system. These attacks can infiltrate systems through various vectors, including compromised downloads, malicious websites, infected USB devices, phishing emails with malicious attachments, and even unsecured IoT devices.
Once installed, malware can perform a range of harmful activities, from data exfiltration and credential harvesting to deploying additional payloads for ransomware or botnet creation. The versatility and adaptability of malware make it a cornerstone of many sophisticated cyberattack campaigns.
Potential impact:
Mitigation:
As businesses increasingly rely on online services, Distributed Denial of Service (DDoS) attacks have become a favoured method for disrupting operations. These attacks flood networks or servers with overwhelming traffic, rendering them inaccessible to legitimate users.
Beyond their immediate disruptive effects, DDoS attacks are often used as a smokescreen to divert attention while attackers execute more invasive activities, such as data breaches or malware deployment.
The increasing accessibility of DDoS-for-hire services has further amplified the threat, enabling attackers to launch large-scale attacks with minimal resources or technical expertise.
Potential impact:
Mitigation:
Understanding the most common cyberthreats is crucial for safeguarding your organisation. Phishing, ransomware, insider threats, malware, and DDoS attacks each present unique challenges, but proactive measures such as employee training, robust technical defences, and regular updates to security protocols can mitigate their impact.
Cybersecurity is a continuous effort that demands vigilance, adaptation, and a culture of awareness. You can protect your business assets, maintain trust, and ensure resilience in an ever-changing threat landscape by staying informed and prepared.
The 2025 Data Privacy Week awareness campaign aims to educate and empower individuals to take control of their personal data.
BUI is proud to announce its commitment to the 2025 Data Privacy Week campaign. As a Data Privacy Week Champion, BUI recognises and supports the principle that all organisations share the responsibility of being conscientious stewards of personal information.
Data Privacy Week is an annual awareness initiative that takes place from 27-31 January. The goal is twofold: to help individuals understand that they have the power to manage their data and to help organisations appreciate why it’s necessary to respect the user data they collect, process, and store.
This year’s theme is Take control of your data – and it’s a timely reminder for everyone as the world becomes more digitally connected, notes BUI Group Governance and Compliance Manager Dhiren Boodhia. “Data Privacy Week highlights the fact that trust is built on transparency. Individuals want to know that their personal information is respected and protected by those who have access to it,” says Boodhia. “As privacy laws and public expectations continue to evolve, organisations should strive to go beyond mere compliance to create a culture of accountability around data privacy and security.”
Your digital activities generate huge amounts of data: websites, apps and online services collect information about your behaviours, your interests, and your purchases. Often, this includes personal data like your identity number and home address. It can even include data about your physical self: think about how smart devices can save health and fitness records as you exercise.
While you cannot control how each byte of data about yourself and your family is shared and processed, you are not helpless! In many cases, you can control how you share your data with a few simple steps. Remember, your personal data is precious and you deserve to be selective about who you share it with. Here are three simple steps to help you manage your data privacy, according to guidelines from the National Cybersecurity Alliance:
Nowadays, when you download a new app, create a new online account, or join a new social media platform, you’ll often be asked for access to your personal information before you can even use it! This data might include your geographic location, contacts, and photos.
For these businesses, personal information about you is tremendously valuable – and you should think about whether the service you get in return is worth the data you must hand over, even if the service is free. Make informed decisions about sharing your data with businesses or third-party service providers… Ask yourself:
For every app, account, or device, check the privacy and security settings. These should be easy to find in the relevant Settings section and should take a few moments to change. Set them to your comfort level for personal information sharing. In general, it’s wise to share less data, not more.
You don’t have to do this for every account at once: start small and over time you’ll make a habit of adjusting all your settings to your comfort level. The National Cybersecurity Alliance has several free resources, including the Manage Your Privacy Settings page, to help you find and check the settings of social media accounts, apps, and more.
Data privacy and data security go hand-in-hand. Along with managing your data privacy settings, remember these four tips to safeguard your information:
During Data Privacy Week this January, we’ll be sharing useful tips and resources to help you become more aware about data privacy at work, at home, and on the move. Follow us on Facebook and LinkedIn so you never miss a post, and join the conversation by using the #DataPrivacyWeek hashtag online.
About Data Privacy Week
Data Privacy Week began as Data Privacy Day in the United States and Canada in January 2008 as an extension of the Data Protection Day celebration in Europe. Data Protection Day commemorates the 28 January 1981 signing of Convention 108, the first legally binding international treaty dealing with privacy and data protection. The National Cybersecurity Alliance, the United States’ leading non-profit, public-private partnership promoting cybersecurity and privacy education and awareness, leads the effort in North America each year. For more information, visit www.staysafeonline.org/data-privacy-week/.
About the National Cybersecurity Alliance
The National Cybersecurity Alliance (NCA) is a non-profit organisation on a mission to create a more secure, interconnected world. The NCA advocates for the safe use of all technology and educates everyone on how best to protect themselves, their families, and their organisations from cybercrime. The NCA creates strong partnerships between governments and corporations to amplify its message and to foster a greater digital good. For more information, visit www.staysafeonline.org.
In Part 2 of our spotlight series on incident response, Zandre Janse van Vuuren explains how to create a comprehensive Incident Response Plan for your organisation.
By Zandre Janse van Vuuren | Service Delivery Manager: Cyber DFIR, BUI
In Part 1, we highlighted the importance of having an Incident Response Plan (IRP) to minimise damage, reduce recovery time, and secure sensitive data during a cybersecurity incident. Now, let’s dive into how to create an effective IRP for your organisation, with practical, step-by-step guidelines you can follow.
The foundation of any effective IRP begins with setting clear objectives and defining the scope. Objectives help align your incident response efforts with your organisation’s goals, risk tolerance, and regulatory requirements. Typical objectives include:
The scope defines the types of incidents the IRP covers and may vary depending on industry standards or regulatory guidelines. For instance, a healthcare provider may need a specific scope for protecting patient data, while a financial institution may focus on transaction security and fraud prevention. By establishing scope early on, you can ensure that your IRP is comprehensive yet focused.
An IRP functions best when it has a well-structured team with clear roles and responsibilities. The team may include internal stakeholders, like IT and management, and external stakeholders, such as legal consultants or third-party security experts.
Each member of your incident response team should have a clearly defined role to prevent delays and confusion during an incident. Roles may include:
Designating these roles upfront helps the team respond more efficiently and cohesively during an incident.
Incidents can range widely in scope and severity, from minor phishing attempts to full-blown data breaches. To streamline response efforts, you must categorise potential incidents and assign impact levels to each. Incident categories could include:
Each category should have multiple impact levels (e.g., low, medium, high) based on criteria like the number of affected systems, potential data loss, and the severity of business impact. This prioritisation ensures critical incidents receive immediate attention, while lower-priority events are handled appropriately without over-allocating resources.
Timely detection and reporting are crucial for an effective IRP. Make sure you implement security tools and monitoring systems that can detect unusual activities or potential threats. There’s a wide range of endpoint protection platforms, network monitoring tools, and intrusion detection systems available for business and enterprise organisations.
Once an incident is detected, a notification protocol outlines how and when incidents should be reported internally and externally.
Make sure you clearly define the people or parties to be notified, the method of notification, and the relevant timeframe.
Containment and eradication are central to limiting an incident’s impact and preventing further damage. Document your procedures for both short-term and long-term containment and eradication.
Both containment and eradication should be documented in detail, tailored to specific incident types, and tested to confirm that they are feasible and effective.
Once the incident is contained and eradicated, recovery efforts aim to return systems to regular operation safely and reliably. The recovery phase may involve restoring affected systems, verifying data integrity, and assessing system functionality. A critical part of this step is to monitor your systems for any indication that the incident may recur, ensuring any residual threats are eliminated.
Remediation actions may also include taking preventative steps, such as reinforcing security controls, updating policies, or providing additional employee training. Documentation is essential here, as lessons learned in recovery and remediation will help improve your IRP over time.
Communication during an incident is essential to inform all stakeholders, control potential reputational damage, and fulfil legal obligations. Your communication strategy should differentiate between internal communications, which provide regular updates to relevant staff, and external communications, which may include notifying customers, partners, regulatory bodies, and the media.
Effective communication strategies often use predefined templates and include guidelines for customising messaging based on the nature and impact of the incident. Designate a spokesperson from your communications or public relations team to ensure consistency and accuracy in your external messages.
Every incident provides a learning opportunity. The post-incident review process aims to evaluate the IRP’s performance, identify areas for improvement, and ensure that lessons are incorporated into the IRP for future incidents.
This step typically includes:
A robust post-incident review process strengthens the IRP and demonstrates a commitment to continuous improvement, which is critical for fostering a proactive security culture and maintaining regulatory compliance.
Bonus tip! The success of any IRP is closely tied to the response team’s performance during high-pressure situations – and that’s why it’s important to cultivate the right mindset. If you and your teammates can maintain your composure, think objectively, and work in unison, then you’ll be ready when it matters most.
With a comprehensive IRP and a teamwork mindset, your organisation will be better equipped to navigate security incidents. Download our checklist to guide you in creating your IRP.
In today’s digital world, it’s not a matter of if but when your organisation will experience a cyber incident. In Part 1 of our incident response spotlight series, Zandre Janse van Vuuren explains why an Incident Response Plan is a critical component of a robust security strategy.
By Zandre Janse van Vuuren | Service Delivery Manager: Cyber DFIR, BUI
In today’s digital world, cybersecurity threats are an ever-present reality. Last year alone, password attacks increased to 4,000 per second (on average) and the number of human-operated ransomware attacks rose by 195 percent. From ransomware to identity breaches, organisations of all sizes are potential targets. The 2024 Microsoft Digital Defense Report (MDDR) puts the growing threat landscape into sharp focus: Microsoft customers face more than 600 million cybercriminal and nation-state attacks every day. While it’s impossible to eliminate the risk of an attack altogether, organisations can significantly reduce the impact by having a well-structured Incident Response Plan in place.
Incident response is not just about reacting to a cyber incident; it’s about being prepared to act swiftly, decisively, and efficiently.
Incident response (IR) planning is the process of developing a structured, documented approach to handling security breaches and cyberattacks. An effective IR plan includes predefined procedures, roles, and responsibilities for responding to and mitigating the effects of cyber incidents. It also outlines communication strategies, legal obligations, and methods for preserving evidence for forensic investigations.
A comprehensive IR plan does far more than provide a structured way to deal with attacks and cyber incidents: it also empowers organisations to be proactive about their security posture.
Incident response is not a one-size-fits-all solution and creating an effective IR plan requires expertise and experience in dealing with complex cyber threats. Our Cyber DFIR team specialises in helping organisations develop, implement, and refine their incident response strategies. When you choose BUI as your security partner, you gain access to seasoned professionals who will work closely with your organisation to:
At BUI, we understand that every organisation faces unique cybersecurity challenges. Our proactive approach ensures that your organisation is prepared, resilient, and capable of responding effectively to any incident. Let our Cyber DFIR team help you safeguard your digital assets and build a stronger security posture through a robust incident response plan. Contact us to get started today.
In October 2023, a significant software security vulnerability was discovered that impacts Microsoft Teams. The vulnerability, designated as CVE-2023-4863, affects not only Microsoft Teams but also Microsoft Edge, Skype for Desktop, and WebP Image Extensions.
Although software updates have been released for Microsoft Teams, Microsoft Defender continues to flag multiple devices as vulnerable. The persistence of this vulnerability is due to the Machine-wide Installer, which installs Teams for all profiles, while deployed updates only update the Teams.exe file for the logged-in user.
While Microsoft does not provide direct remediation for this specific issue, there are steps you can take to address it. Although manual remediation via scripting may not be ideal, a script released on GitHub by Lee Vilenski has proven to be very successful.

We have modified Vilenski’s script to meet our requirements and deployment methods, as shown below. The original script can be found here.
# Define minimum acceptable version (replace with your desired version)
$minVersion = “1.7.00.8651”
############### Do Not Edit Below This Line #################################
###Finding SIDs for loop
# Regex pattern for SIDs
$PatternSID = ‘S-1-5-21-\d+-\d+\-\d+\-\d+$’
# Get Username, SID, and location of ntuser.dat for all users
$ProfileList = gp ‘HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\*’ | Where-Object {$_.PSChildName -match $PatternSID} |
Select @{name=”SID”;expression={$_.PSChildName}},
@{name=”UserHive”;expression={“$($_.ProfileImagePath)\ntuser.dat”}},
@{name=”Username”;expression={$_.ProfileImagePath -replace ‘^(.*[\\\/])’, ”}}
# Get all user SIDs found in HKEY_USERS (ntuder.dat files that are loaded)
$LoadedHives = gci Registry::HKEY_USERS | ? {$_.PSChildname -match $PatternSID} | Select @{name=”SID”;expression={$_.PSChildName}}
# Get all users that are not currently logged
$UnloadedHives = Compare-Object $ProfileList.SID $LoadedHives.SID | Select @{name=”SID”;expression={$_.InputObject}}, UserHive, Username
# Loop through each profile on the machine
Foreach ($item in $ProfileList) {
# Load User ntuser.dat if it’s not already loaded
IF ($item.SID -in $UnloadedHives.SID) {
reg load HKU\$($Item.SID) $($Item.UserHive) | Out-Null
}
#####################################################################
# Check and potentially remove outdated Teams versions
# Get Teams uninstall keys for the user
$teamsUninstallKeys = Get-ItemProperty registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\Teams*
if ($teamsUninstallKeys) {
foreach ($teamsKey in $teamsUninstallKeys) {
# Check DisplayVersion and remove key if outdated (with confirmation)
$displayVersion = $teamsKey.DisplayVersion
if ($displayVersion -lt $minVersion) {
$uninstallString = “C:\Users\$($item.Username)\appdata\local\microsoft\teams\update”
# Consider error handling for uninstall process (not shown here)
try {
Start-Process -FilePath $uninstallString -ArgumentList “–uninstall” -Wait -Verb RunAsAdministrator
} catch {
}
# Remove the Teams uninstall key (use with caution)
Remove-Item -Path “registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\$($teamsKey.PSName)” -Recurse}
}
} # Unload ntuser.dat
IF ($item.SID -in $UnloadedHives.SID) {
[gc]::Collect()
reg unload HKU\$($item.SID) | Out-Null
}
}
################## Remove Teams where Regkey doesn’t exist #############################
$userProfiles = Get-ChildItem -Path “C:\Users” -Directory -Exclude Default,Public
# Loop through each user profile
foreach ($profile in $userProfiles) {
# Check if Teams executable exists
$teamsPath = Join-Path -Path $profile.FullName -ChildPath “AppData\Local\Microsoft\Teams\current\Teams.exe”
if (Test-Path $teamsPath) {
# Get the installed version
$installedVersion = (Get-ItemProperty $teamsPath).VersionInfo.FileVersion
# Check version – inform about outdated and above versions
if ($installedVersion -lt $minVersion) {
Write-Host “Outdated Teams version found in $($profile): $installedVersion”
# Uninstall Teams (requires admin privileges)
Remove-Item -Path $teamsPath -Recurse -Force -ErrorAction SilentlyContinue
if ($?) {
Write-Host “Uninstalled Teams from $profile successfully.”
} else {
Write-Host “Failed to uninstall Teams from $profile.”
}
} else {
Write-Host “Teams version in $profile ($installedVersion) is above or meets the minimum requirement.”
}
}
}
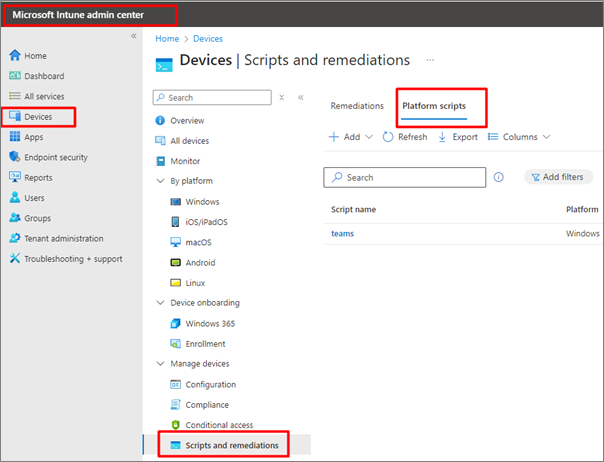
3. Select Add/Create to create a new script, select Windows 10 and later
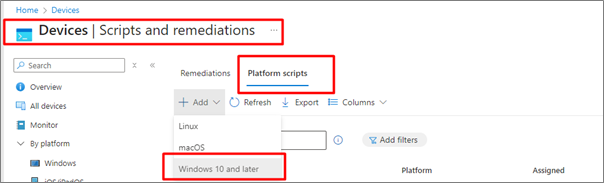
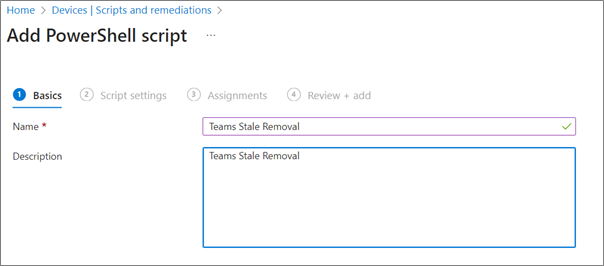
4. Enter Name and Description for script
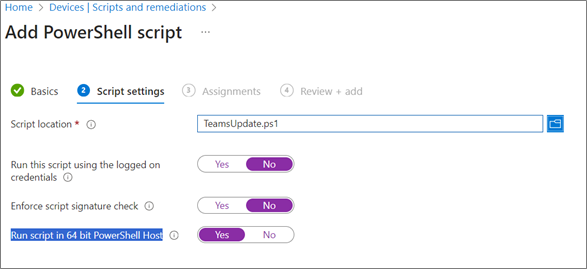
5. Under script settings:
6. On next screen, Assign the script to the All devices group
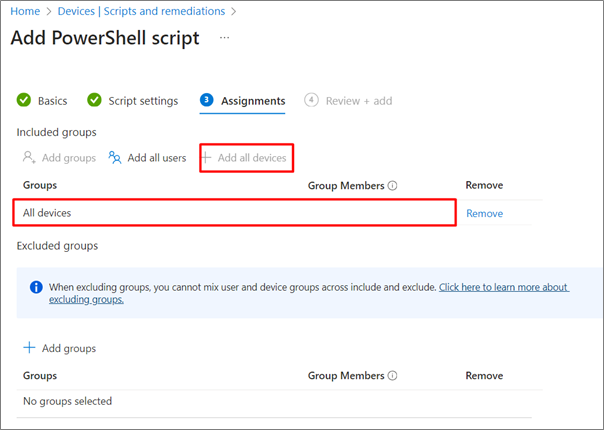
7. Save
By BUI SecOps Principal Technical Consultant, Terryanne du Toit and BUI SecOps Technical Consultant, Danie Miller.
By Neil du Plessis | Cloud Security Architect, BUI
The artificial intelligence that powers Copilot for Microsoft 365 is also used in neighbouring Microsoft technologies for the modern workplace. Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security are either coming soon or already available to Business and Enterprise customers. Let’s take a closer look at each one.
Microsoft describes Copilot for Azure as an AI-powered assistant that simplifies the design, operation, optimisation, and troubleshooting of applications and infrastructure within the Azure ecosystem. It utilises Large Language Models, the Azure control plane, and insights about your Azure and Azure Arc-enabled assets to help you streamline cloud orchestration and management.
Highlights: Copilot for Azure can help you design and develop your cloud applications, choose the best frameworks, languages, and tools, and test and debug your code. It can also help you deploy and manage your applications by providing automation, scalability, and monitoring. In addition, Copilot for Azure can recommend ways to optimise costs and improve security and compliance in your environment.
Availability: Copilot for Azure is currently in preview, and existing Azure customers and Microsoft Partners can apply to participate. If you’re interested, review the registration process before filling in the application form.
Copilot for Sales is designed to help your sales teams boost productivity, improve customer engagements, and close more deals. It takes the foundational capabilities of Copilot for Microsoft 365 and enhances them by connecting to customer relationship management platforms (like Microsoft Dynamics 365 Sales and Salesforce Sales Cloud) and providing sales teams with relevant in-app insights and recommendations to enhance customer interactions.
Highlights: According to Microsoft, Copilot for Sales empowers your sellers to simplify daily tasks, personalise customer interactions, and streamline workflows. From drafting emails in Outlook and setting up meetings in Teams to creating pitch decks in PowerPoint and data visualisations in Excel, Copilot for Sales is geared to help sales teams accomplish more in less time with AI-powered communication, content, and CRM activities.
Availability: Copilot for Sales is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Sales for an additional $20 per user per month. The Copilot for Sales pricing guide has further details, terms, and conditions.
Copilot for Service applies artificial intelligence to your call centre operations to help your customer service and support teams handle customer interactions more efficiently. Copilot for Service brings together all relevant content from your CRM platforms, websites, SharePoint sites, and third-party knowledge bases (like Salesforce, ServiceNow, and Zendesk) and puts it at your agents’ fingertips through conversational AI.
Highlights: Your customer service and support teams can enter natural language prompts and Copilot for Service will generate answers based on your organisational content – from call centre playbooks and user manuals to customer records and case histories in your CRM tools. Your agents can do this in their flow of work during real-time engagements with customers to handle queries faster, resolve issues earlier, and improve customer satisfaction over time.
Availability: Copilot for Service is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Service for an additional $20 per user per month. The Copilot for Service pricing guide has further details, terms, and conditions.
Unveiled by Microsoft at the 2023 Microsoft Ignite conference, Microsoft Copilot Studio is a low-code tool that enables you to tailor Copilot for Microsoft 365 and build your own AI-driven copilots by leveraging conversational features like custom GPTs and generative AI plugins.
Highlights: With Microsoft Copilot Studio, you’re able to personalise Copilot for Microsoft 365 according to your business needs. You can develop, test, and publish standalone copilots and regulate and secure them with the appropriate permissions, data access, and user controls. You can also see the end-to-end lifecycle of your customisations and standalone copilots in one place, which makes building, deploying, managing, and analysing them easier and simpler. In addition, you can use Microsoft Copilot Studio to link Copilot to other data sources to access any system of record, including SAP, ServiceNow, and Workday.
Availability: Microsoft Copilot Studio is available now, and the integration with Copilot for Microsoft 365 is currently in public preview. The Microsoft Copilot Studio website has further details, terms, and conditions.
Microsoft Copilot for Security was also announced at the 2023 Microsoft Ignite conference, where Microsoft explained it as an AI-powered cybersecurity product that “enables security professionals to respond to cyberthreats quickly, process signals at machine speed, and assess risk exposure in minutes”.
Highlights: Microsoft Copilot for Security combines an advanced Large Language Model with a security-specific model informed by Microsoft’s unique global threat intelligence and more than 65 trillion daily signals. The result is a sophisticated, security-focused AI assistant that can provide actionable responses to your natural language questions. These responses can be in the form of text, code, or a visual that helps you understand the full context of a security incident, its impact, and the next steps you should take for remediation and defence hardening.
Availability: Microsoft Copilot for Security is currently in private preview through an invitation-only Early Access Programme for customers and Microsoft Partners. BUI is participating in the Microsoft Copilot for Security Partner Private Preview, and is working with Microsoft product teams to help shape product development. Learn more in our news update.
With Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security, Microsoft is expanding its range of AI-powered technologies to help you streamline cloud orchestration and management, boost sales productivity, improve customer service, spur innovation, and secure your data and resources. The sooner you start exploring these tools, the sooner you’ll be ready to empower your teams for even greater success.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
Terms and Conditions for this security vulnerability disclosure blog:
Microsoft Defender XDR is a comprehensive cybersecurity solution designed by Microsoft to protect organisational networks and devices. At its core are the Attack Surface Reduction (ASR) rules, which are strategic security protocols aimed at minimising the vulnerabilities and pathways exploited by cyber threats. These rules act as a crucial line of defence, shielding endpoints from various attack vectors such as malicious documents, scripts, and other potentially harmful activities. However, despite their importance in fortifying cybersecurity defences, recent scrutiny has uncovered a critical vulnerability within these ASR rules. This vulnerability poses a significant risk as it allows adversaries to bypass established security measures without triggering alerts or raising suspicion, thereby compromising the effectiveness of Microsoft Defender XDR’s defence mechanisms.
Regrettably, a remedy for this issue is not yet available*. Consequently, recourse to Advanced Hunting queries armed with Custom detection rules becomes imperative to diligently monitor for any indicators of compromise, thereby mitigating potential risks.
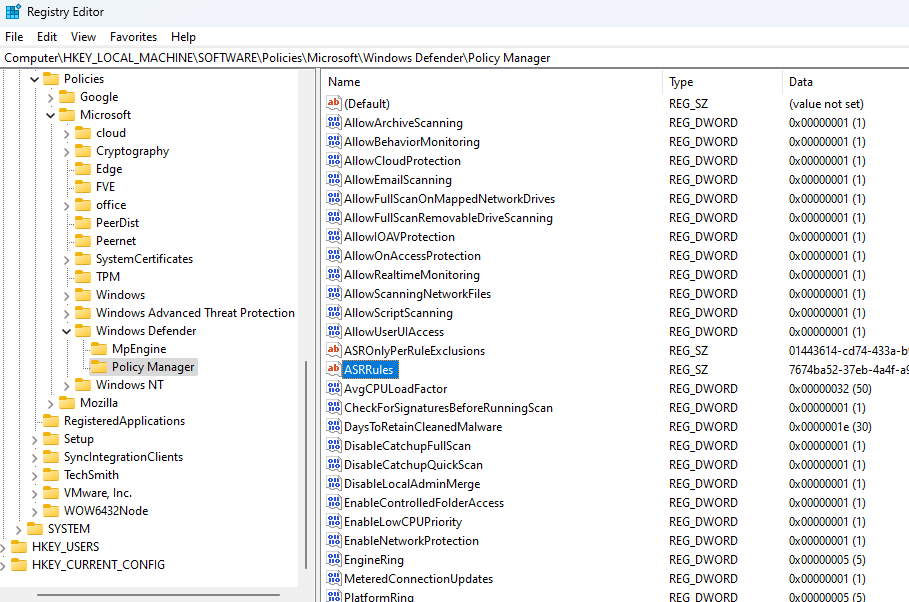
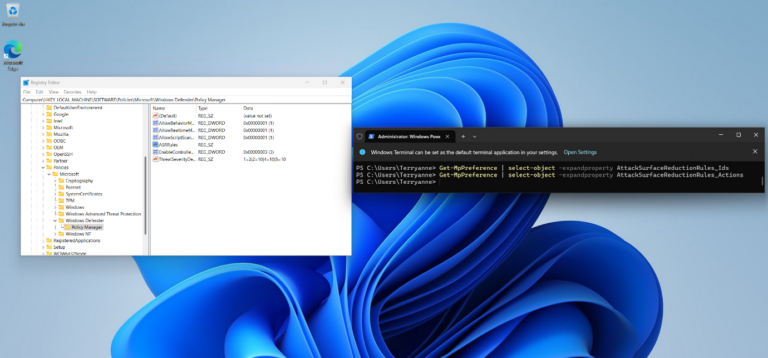
Attack Surface Reduction (ASR) rules are configured on devices by means of a registry key. The contents of this key include the GUID for the specific ASR rule as well as the state of the rule (Block, Audit).
The registry key is not protected and can be modified without triggering any alerts, essentially bypassing ASR rules, which could result in negation of the protection.
Registry Key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
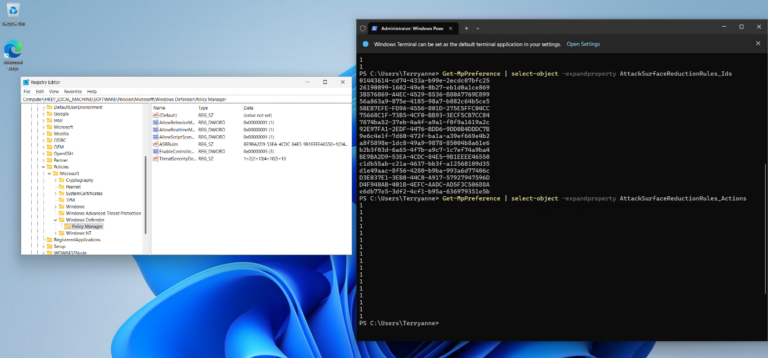
By following the steps below, ASR rules can be bypassed. The rule Block all Office applications from creating child processes will be tested.
Bypassing ASR rules:
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\
ASR Rules
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Ids
Get-MpPreference | Select-Object -expandproperty AttackSurfaceReductionRules_Actions
Testing the bypass:
Example: Mkdir “c:\tools\new folder”
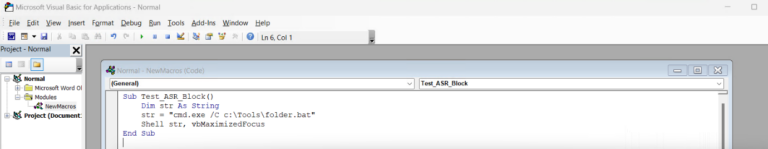
Sub [your Macro name] ()
Dim str As String
Str = “cmd.exe /C [location of bat file] ”
shell str, vbMaximizedFocus
End Sub
Example shown here in screenshot:
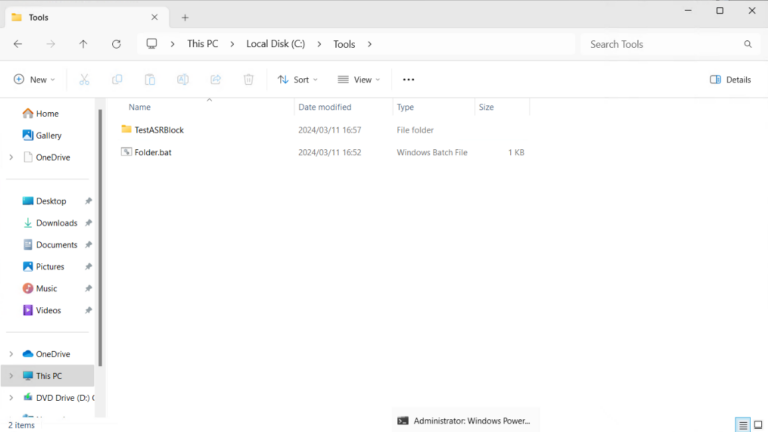
The successful creation of a folder indicates that ASR rules have been successfully bypassed.
Running the same Macro without bypassing the ASR rules results in the following alert:
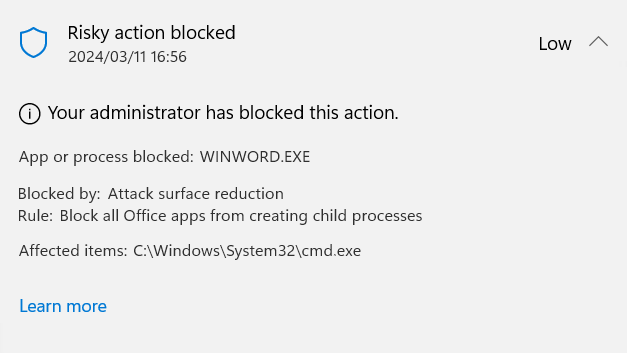
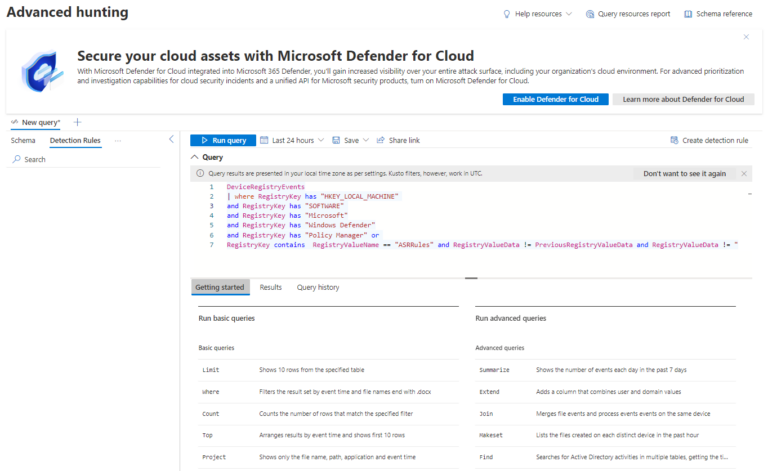
By determining the current ASR policy configuration and monitoring for any changes to this configuration, Advanced Hunting queries with Custom detection rules can act as a potential mitigation strategy until this critical vulnerability is remediated.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Policy Manager\ASR Rules
DeviceRegistryEvents
| where RegistryKey has “HKEY_LOCAL_MACHINE”
and RegistryKey has “SOFTWARE”
and RegistryKey has “Microsoft”
and RegistryKey has “Windows Defender”
and RegistryKey has “Policy Manager” or
RegistryKey contains RegistryValueName == “ASRRules” and RegistryValueData != PreviousRegistryValueData and RegistryValueData != “ [Enter your registry key value here] ”
Suggested configurations:
Frequency: Every hour
Impacted Entity: Device | Device ID
Actions: Run antivirus scan
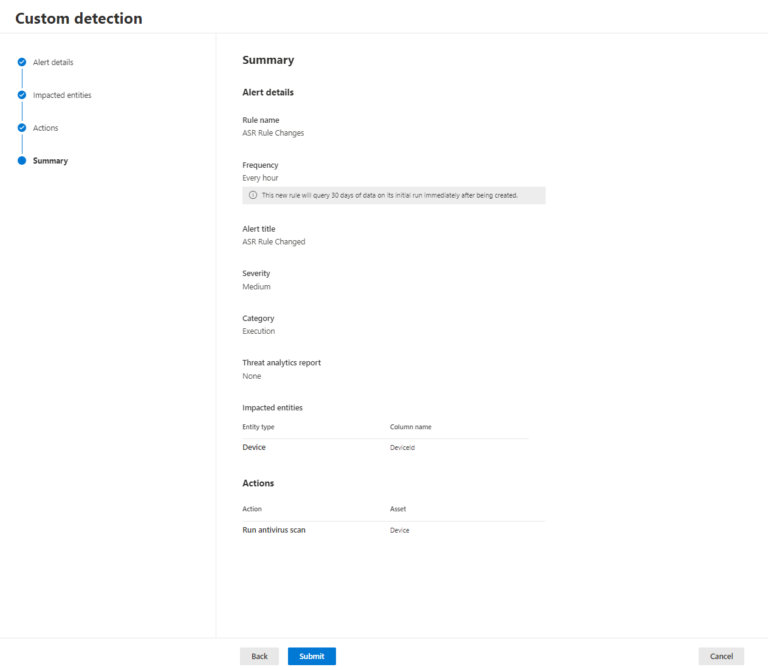
Once configured, the Custom detection rule will run once every hour and generate an alert for all devices in which the ASR rule registry key has changed.
Any alerts should be investigated as running a Microsoft Defender Antivirus scan alone will not be a sufficient response.
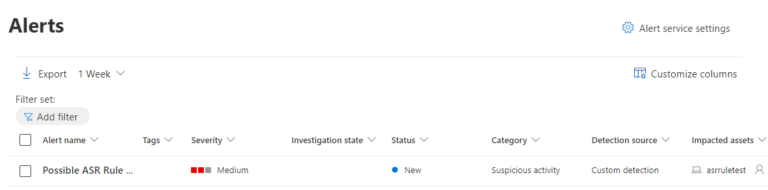
It is important to note that the registry key in the Advanced Hunting query should be updated after any change is made to the ASR rules.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365 is an innovative tool that can transform how you work with computers. However, as with any new technology, it requires some preparation and adaptation on your part to ensure the most beneficial results in the long run.
Jared Spataro, the Corporate Vice President of Modern Work and Business Applications at Microsoft, once said that “becoming an AI-powered organisation doesn’t happen with the flip of a switch”. And he was right: you have to understand Copilot’s features and functionality before you can harness its full potential. Here are three important steps in the preparation journey.
Copilot is a powerful AI assistant that can help you with numerous tasks and activities in your Microsoft 365 apps, but it’s not a magic solution to every problem. You will need to learn how to use Copilot effectively – by composing clear prompts, providing relevant details and parameters, and reviewing and refining outputs.
You’ll also need to explore the frameworks guiding and controlling Copilot so that you understand how data security policies, privacy policies, and responsible AI checks are applied. Fortunately, there are plenty of resources available online, from technical documentation to in-depth tutorials and walkthroughs. You can also watch these introductory videos to see how Copilot for Microsoft 365 works:

Even though Copilot can help you augment your capabilities, it’s no substitute for your unique human intelligence. Remember that Copilot uses generative artificial intelligence to draft responses to your prompts, providing an output based on your input.
A well-structured, specific prompt with appropriate context will yield a more accurate result than a vague query. If you take the time to develop your prompt engineering skills and evaluate, analyse, and even interrogate Copilot’s output, you’ll be better prepared to use the tool properly.
It’s also essential to apply your professional judgement, ethical standards, and niche industry or domain knowledge to your tasks and projects with Copilot. After all, the tool doesn’t have the benefit of your personal experience, expertise, or emotion.
Copilot is designed to be your digital assistant. Your AI sidekick. Your know-a-lot companion in Excel, Outlook, PowerPoint, Teams, and Word. But there will be a learning curve at the beginning – for you and the tool.
Because Copilot learns from context and adapts over time, it may not generate perfect responses to your queries from the start. You’ll need to experiment with different prompts and fine-tune your inputs to get high-quality outputs, so keep practising.
It’s also a good idea to join an online forum or community group of fellow Copilot users in your industry to take advantage of their shared knowledge, resources, and tips for success. The Copilot for Microsoft 365 community on the Microsoft Tech Community website is filled with news updates, event details, and discussions related to Copilot for Microsoft 365.
Learning how to use Copilot effectively, developing your prompt engineering and critical thinking skills, and tapping into the knowledge of fellow Copilot users can help you prepare for a new world of work with this AI-powered helper by your side.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
More than three-quarters of early users said that once they tried Copilot for Microsoft 365, they didn’t want to give it up. Why? Because having this AI-powered assistant as their workplace aide helped them to save time, unleash their creativity, enhance their skills, and unlock the full potential of their favourite Microsoft 365 apps.
In the Work Trend Index Special Report published by Microsoft last year, the same early users said that Copilot for Microsoft 365 empowered them to do more – and do it more efficiently than before. From creating presentations in PowerPoint to managing emails in Outlook, Copilot helped them achieve their goals.
But how exactly can Copilot for Microsoft 365 help you and your teams? How can you take advantage of this technology in your business right now? Let’s explore three everyday use cases for Copilot for Microsoft 365 in the modern workplace.
Whether you need to write a blog post, a newsletter, a proposal, or a summary, Copilot can help you with the creative process.
You can tell Copilot to draft an outline, a title, a hook, or a conclusion for your document based on your topic and purpose. You can get Copilot to check your grammar and spelling and edit, rewrite, or paraphrase your text to improve the tone, style, and clarity.
You can also direct Copilot to help you with formatting, referencing, and citing your sources so that your entire document is eye-catching, precise, and correctly attributed.
With Copilot as your co-creator, you can speed up the writing process and craft compelling content that meets your needs. Watch these videos for a closer look at what’s possible with Copilot in Word.
Whether you need to work with numbers, charts, tables, or graphs, Copilot can help you with data analysis and presentation.
You can get Copilot to perform calculations, apply formulas, filter data, or create pivot tables in Excel, based on your data set and goal.
You can ask Copilot to help you interpret and make sense of your data by providing summaries, trends, or insights in natural language.
You can also use Copilot to generate charts and graphs so that you can visualise your data, highlight relevant information, and vividly present your findings.
With Copilot by your side in Excel, you can enhance the way you work with and analyse data. Watch these videos to see how Copilot filters, formats, and reviews data.
Whether you need to plan a project, schedule a meeting, or follow up on an email, Copilot can help you with task management and day-to-day organisation.
You can ask Copilot to create a project plan, a timeline, or a checklist in Word, Excel, or PowerPoint, based on your project scope and deliverables.
You can instruct Copilot to schedule a meeting, send an invitation to your chosen attendees, and create an agenda to match the meeting topic – all from within Outlook or Teams.
You can also get Copilot to help you respond to emails, create tasks, and set reminders in Outlook or Teams, based on your email content and priorities.
With Copilot as your digital assistant, you can stay on top of your tasks and organise your calendar more efficiently. Watch these videos for an overview of Copilot’s functionality in Outlook and Teams.
Real-time intelligent assistance from Copilot for Microsoft 365 enables people to work more creatively and productively. More than 80% of surveyed users said Copilot makes it easier to get started on a first draft; take action after a meeting; and catch up on what they missed. More than 70% said Copilot helped them complete work faster and save time on mundane tasks. And 68% said Copilot improved the quality of their work.
Going forward, those who embrace Copilot for Microsoft 365 as an ally at work and take the time to build new digital habits will benefit the most from this powerful technology.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365, the advanced AI assistant embedded in Microsoft 365 apps like PowerPoint and Word, made waves in workplaces worldwide after it was ANNOUNCED IN 2023.
The tool enables people to perform tasks and generate content using natural language commands and is ALREADY CONSIDERED A GAME-CHANGER for productivity and human-computer interaction, even as Microsoft continues to refine its capabilities and features.
So, what can we expect from this innovative technology going forward? Here are four important updates to know about Copilot for Microsoft 365.
On 1 November last year, Microsoft made Copilot for Microsoft 365 available to Microsoft 365 customers on Enterprise plans. Since then, Microsoft has removed the Microsoft 365 prerequisite and minimum-purchase restrictions to expand its Copilot for Microsoft 365 licensing model to include enterprises using Office 365 E3/E5 and small and medium-sized businesses (SMBs).
As of 15 January 2024, Enterprise customers (Office 365 E3, Office 365 E5, Microsoft 365 E3 and Microsoft 365 E5) and Business customers (Microsoft 365 Business Standard and Microsoft 365 Business Premium) can purchase Copilot for Microsoft 365 as an add-on to an existing subscription for $30 per user per month.
Initially, Copilot was only available in English for users based in the United States, Canada, and the United Kingdom. Today, it’s available in 36 regions across the Americas, Europe, Africa, and Asia, and Microsoft is working hard to expand both audience and market reach.
In addition to English, Copilot for Microsoft 365 is supported in Chinese (Simplified), French, German, Italian, Japanese, Portuguese, and Spanish. Microsoft plans to support several more languages over the first half of 2024, including Arabic, Chinese (Traditional), Czech, Danish, Dutch, Finnish, Hebrew, Hungarian, Korean, Norwegian, Polish, Russian, Swedish, Thai, Turkish, and Ukrainian.

Microsoft is enhancing the workplace value of Copilot for Microsoft 365 by adding new features and integrating it with more apps and services – both inside and outside of the Microsoft 365 suite. For example, Copilot works seamlessly with Loop and SharePoint, and is coming soon in Planner, OneNote, and Stream to allow users to access and manage files and tasks through natural language prompts and queries.
Copilot can also connect with third-party apps and services, including Salesforce, Jira, Dynamics 365, Bing Web Search, ServiceNow, and Zendesk, enabling users to perform actions and gather external information without leaving their current app.
Copilot can also leverage the power of the Microsoft Graph and third-party integrated applications like SQL and Confluence to provide users with personalised, contextual suggestions and insights based on their preferences, history, and activity.
Microsoft is committed to improving Copilot for Microsoft 365 so that it consistently produces relevant, high-quality output for users based on their prompts and context. To achieve this, Microsoft has been refining Copilot’s processing and orchestration engine, updating its Large Language Models, and gathering public and partner feedback through early access programmes, preview programmes, and dedicated community forums like the Copilot Feedback Hub, where users can share their observations, suggestions, and experiences with the tool.
These efforts continue to yield results: Copilot’s accuracy and reliability have improved significantly since launch; 70% of early users have reported increased personal productivity; and 77% of early users have said that once they used Copilot, they didn’t want to give it up.
With its expanded licensing model, broader language support, increased integration with apps and services, and improved accuracy and reliability, Copilot for Microsoft 365 is set to become a critical tool for businesses of all sizes.
As Microsoft further refines Copilot’s capabilities and features, we can expect this AI-powered assistant to revolutionise organisations everywhere by empowering people to do more with their favourite Microsoft 365 apps every day.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.