In October 2023, a significant software security vulnerability was discovered that impacts Microsoft Teams. The vulnerability, designated as CVE-2023-4863, affects not only Microsoft Teams but also Microsoft Edge, Skype for Desktop, and WebP Image Extensions.
Although software updates have been released for Microsoft Teams, Microsoft Defender continues to flag multiple devices as vulnerable. The persistence of this vulnerability is due to the Machine-wide Installer, which installs Teams for all profiles, while deployed updates only update the Teams.exe file for the logged-in user.
While Microsoft does not provide direct remediation for this specific issue, there are steps you can take to address it. Although manual remediation via scripting may not be ideal, a script released on GitHub by Lee Vilenski has proven to be very successful.

We have modified Vilenski’s script to meet our requirements and deployment methods, as shown below. The original script can be found here.
# Define minimum acceptable version (replace with your desired version)
$minVersion = “1.7.00.8651”
############### Do Not Edit Below This Line #################################
###Finding SIDs for loop
# Regex pattern for SIDs
$PatternSID = ‘S-1-5-21-\d+-\d+\-\d+\-\d+$’
# Get Username, SID, and location of ntuser.dat for all users
$ProfileList = gp ‘HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\*’ | Where-Object {$_.PSChildName -match $PatternSID} |
Select @{name=”SID”;expression={$_.PSChildName}},
@{name=”UserHive”;expression={“$($_.ProfileImagePath)\ntuser.dat”}},
@{name=”Username”;expression={$_.ProfileImagePath -replace ‘^(.*[\\\/])’, ”}}
# Get all user SIDs found in HKEY_USERS (ntuder.dat files that are loaded)
$LoadedHives = gci Registry::HKEY_USERS | ? {$_.PSChildname -match $PatternSID} | Select @{name=”SID”;expression={$_.PSChildName}}
# Get all users that are not currently logged
$UnloadedHives = Compare-Object $ProfileList.SID $LoadedHives.SID | Select @{name=”SID”;expression={$_.InputObject}}, UserHive, Username
# Loop through each profile on the machine
Foreach ($item in $ProfileList) {
# Load User ntuser.dat if it’s not already loaded
IF ($item.SID -in $UnloadedHives.SID) {
reg load HKU\$($Item.SID) $($Item.UserHive) | Out-Null
}
#####################################################################
# Check and potentially remove outdated Teams versions
# Get Teams uninstall keys for the user
$teamsUninstallKeys = Get-ItemProperty registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\Teams*
if ($teamsUninstallKeys) {
foreach ($teamsKey in $teamsUninstallKeys) {
# Check DisplayVersion and remove key if outdated (with confirmation)
$displayVersion = $teamsKey.DisplayVersion
if ($displayVersion -lt $minVersion) {
$uninstallString = “C:\Users\$($item.Username)\appdata\local\microsoft\teams\update”
# Consider error handling for uninstall process (not shown here)
try {
Start-Process -FilePath $uninstallString -ArgumentList “–uninstall” -Wait -Verb RunAsAdministrator
} catch {
}
# Remove the Teams uninstall key (use with caution)
Remove-Item -Path “registry::HKEY_USERS\$($item.SID)\Software\Microsoft\Windows\CurrentVersion\Uninstall\$($teamsKey.PSName)” -Recurse}
}
} # Unload ntuser.dat
IF ($item.SID -in $UnloadedHives.SID) {
[gc]::Collect()
reg unload HKU\$($item.SID) | Out-Null
}
}
################## Remove Teams where Regkey doesn’t exist #############################
$userProfiles = Get-ChildItem -Path “C:\Users” -Directory -Exclude Default,Public
# Loop through each user profile
foreach ($profile in $userProfiles) {
# Check if Teams executable exists
$teamsPath = Join-Path -Path $profile.FullName -ChildPath “AppData\Local\Microsoft\Teams\current\Teams.exe”
if (Test-Path $teamsPath) {
# Get the installed version
$installedVersion = (Get-ItemProperty $teamsPath).VersionInfo.FileVersion
# Check version – inform about outdated and above versions
if ($installedVersion -lt $minVersion) {
Write-Host “Outdated Teams version found in $($profile): $installedVersion”
# Uninstall Teams (requires admin privileges)
Remove-Item -Path $teamsPath -Recurse -Force -ErrorAction SilentlyContinue
if ($?) {
Write-Host “Uninstalled Teams from $profile successfully.”
} else {
Write-Host “Failed to uninstall Teams from $profile.”
}
} else {
Write-Host “Teams version in $profile ($installedVersion) is above or meets the minimum requirement.”
}
}
}
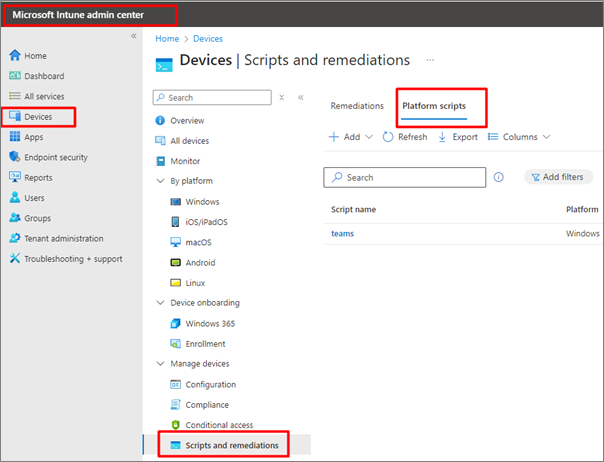
3. Select Add/Create to create a new script, select Windows 10 and later
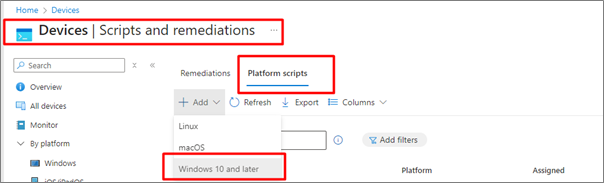
4. Enter Name and Description for script
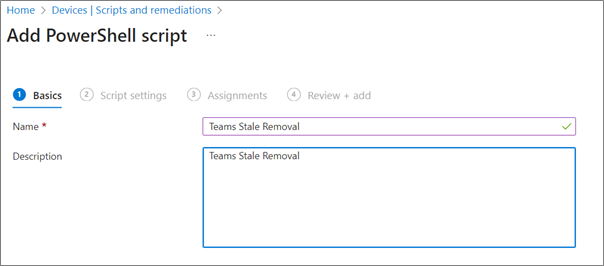
5. Under script settings:
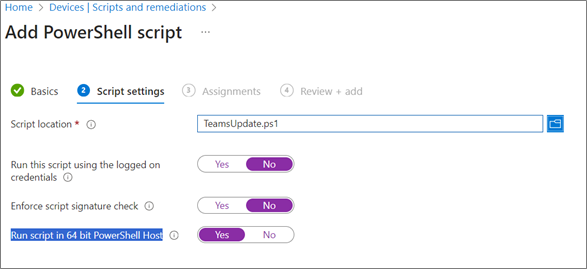
6. On next screen, Assign the script to the All devices group
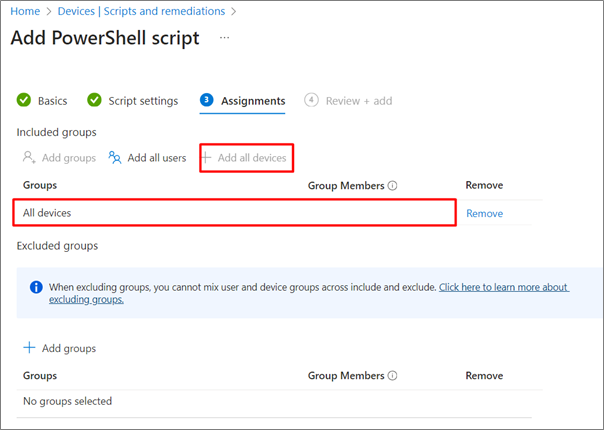
7. Save
By BUI SecOps Principal Technical Consultant, Terryanne du Toit and BUI SecOps Technical Consultant, Danie Miller.
By Neil du Plessis | Cloud Security Architect, BUI
The artificial intelligence that powers Copilot for Microsoft 365 is also used in neighbouring Microsoft technologies for the modern workplace. Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security are either coming soon or already available to Business and Enterprise customers. Let’s take a closer look at each one.
Microsoft describes Copilot for Azure as an AI-powered assistant that simplifies the design, operation, optimisation, and troubleshooting of applications and infrastructure within the Azure ecosystem. It utilises Large Language Models, the Azure control plane, and insights about your Azure and Azure Arc-enabled assets to help you streamline cloud orchestration and management.
Highlights: Copilot for Azure can help you design and develop your cloud applications, choose the best frameworks, languages, and tools, and test and debug your code. It can also help you deploy and manage your applications by providing automation, scalability, and monitoring. In addition, Copilot for Azure can recommend ways to optimise costs and improve security and compliance in your environment.
Availability: Copilot for Azure is currently in preview, and existing Azure customers and Microsoft Partners can apply to participate. If you’re interested, review the registration process before filling in the application form.
Copilot for Sales is designed to help your sales teams boost productivity, improve customer engagements, and close more deals. It takes the foundational capabilities of Copilot for Microsoft 365 and enhances them by connecting to customer relationship management platforms (like Microsoft Dynamics 365 Sales and Salesforce Sales Cloud) and providing sales teams with relevant in-app insights and recommendations to enhance customer interactions.
Highlights: According to Microsoft, Copilot for Sales empowers your sellers to simplify daily tasks, personalise customer interactions, and streamline workflows. From drafting emails in Outlook and setting up meetings in Teams to creating pitch decks in PowerPoint and data visualisations in Excel, Copilot for Sales is geared to help sales teams accomplish more in less time with AI-powered communication, content, and CRM activities.
Availability: Copilot for Sales is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Sales for an additional $20 per user per month. The Copilot for Sales pricing guide has further details, terms, and conditions.
Copilot for Service applies artificial intelligence to your call centre operations to help your customer service and support teams handle customer interactions more efficiently. Copilot for Service brings together all relevant content from your CRM platforms, websites, SharePoint sites, and third-party knowledge bases (like Salesforce, ServiceNow, and Zendesk) and puts it at your agents’ fingertips through conversational AI.
Highlights: Your customer service and support teams can enter natural language prompts and Copilot for Service will generate answers based on your organisational content – from call centre playbooks and user manuals to customer records and case histories in your CRM tools. Your agents can do this in their flow of work during real-time engagements with customers to handle queries faster, resolve issues earlier, and improve customer satisfaction over time.
Availability: Copilot for Service is available now for $50 per user per month, which includes the requisite Copilot for Microsoft 365 licence. If you already have Copilot for Microsoft 365 (via your Office 365 E3, Office 365 E5, Microsoft 365 E3, Microsoft 365 E5, Microsoft 365 Business Standard, or Microsoft 365 Business Premium subscription), then you can get Copilot for Service for an additional $20 per user per month. The Copilot for Service pricing guide has further details, terms, and conditions.
Unveiled by Microsoft at the 2023 Microsoft Ignite conference, Microsoft Copilot Studio is a low-code tool that enables you to tailor Copilot for Microsoft 365 and build your own AI-driven copilots by leveraging conversational features like custom GPTs and generative AI plugins.
Highlights: With Microsoft Copilot Studio, you’re able to personalise Copilot for Microsoft 365 according to your business needs. You can develop, test, and publish standalone copilots and regulate and secure them with the appropriate permissions, data access, and user controls. You can also see the end-to-end lifecycle of your customisations and standalone copilots in one place, which makes building, deploying, managing, and analysing them easier and simpler. In addition, you can use Microsoft Copilot Studio to link Copilot to other data sources to access any system of record, including SAP, ServiceNow, and Workday.
Availability: Microsoft Copilot Studio is available now, and the integration with Copilot for Microsoft 365 is currently in public preview. The Microsoft Copilot Studio website has further details, terms, and conditions.
Microsoft Copilot for Security was also announced at the 2023 Microsoft Ignite conference, where Microsoft explained it as an AI-powered cybersecurity product that “enables security professionals to respond to cyberthreats quickly, process signals at machine speed, and assess risk exposure in minutes”.
Highlights: Microsoft Copilot for Security combines an advanced Large Language Model with a security-specific model informed by Microsoft’s unique global threat intelligence and more than 65 trillion daily signals. The result is a sophisticated, security-focused AI assistant that can provide actionable responses to your natural language questions. These responses can be in the form of text, code, or a visual that helps you understand the full context of a security incident, its impact, and the next steps you should take for remediation and defence hardening.
Availability: Microsoft Copilot for Security is currently in private preview through an invitation-only Early Access Programme for customers and Microsoft Partners. BUI is participating in the Microsoft Copilot for Security Partner Private Preview, and is working with Microsoft product teams to help shape product development. Learn more in our news update.
With Copilot for Azure, Copilot for Sales, Copilot for Service, Microsoft Copilot Studio, and Microsoft Copilot for Security, Microsoft is expanding its range of AI-powered technologies to help you streamline cloud orchestration and management, boost sales productivity, improve customer service, spur innovation, and secure your data and resources. The sooner you start exploring these tools, the sooner you’ll be ready to empower your teams for even greater success.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365 is an innovative tool that can transform how you work with computers. However, as with any new technology, it requires some preparation and adaptation on your part to ensure the most beneficial results in the long run.
Jared Spataro, the Corporate Vice President of Modern Work and Business Applications at Microsoft, once said that “becoming an AI-powered organisation doesn’t happen with the flip of a switch”. And he was right: you have to understand Copilot’s features and functionality before you can harness its full potential. Here are three important steps in the preparation journey.
Copilot is a powerful AI assistant that can help you with numerous tasks and activities in your Microsoft 365 apps, but it’s not a magic solution to every problem. You will need to learn how to use Copilot effectively – by composing clear prompts, providing relevant details and parameters, and reviewing and refining outputs.
You’ll also need to explore the frameworks guiding and controlling Copilot so that you understand how data security policies, privacy policies, and responsible AI checks are applied. Fortunately, there are plenty of resources available online, from technical documentation to in-depth tutorials and walkthroughs. You can also watch these introductory videos to see how Copilot for Microsoft 365 works:

Even though Copilot can help you augment your capabilities, it’s no substitute for your unique human intelligence. Remember that Copilot uses generative artificial intelligence to draft responses to your prompts, providing an output based on your input.
A well-structured, specific prompt with appropriate context will yield a more accurate result than a vague query. If you take the time to develop your prompt engineering skills and evaluate, analyse, and even interrogate Copilot’s output, you’ll be better prepared to use the tool properly.
It’s also essential to apply your professional judgement, ethical standards, and niche industry or domain knowledge to your tasks and projects with Copilot. After all, the tool doesn’t have the benefit of your personal experience, expertise, or emotion.
Copilot is designed to be your digital assistant. Your AI sidekick. Your know-a-lot companion in Excel, Outlook, PowerPoint, Teams, and Word. But there will be a learning curve at the beginning – for you and the tool.
Because Copilot learns from context and adapts over time, it may not generate perfect responses to your queries from the start. You’ll need to experiment with different prompts and fine-tune your inputs to get high-quality outputs, so keep practising.
It’s also a good idea to join an online forum or community group of fellow Copilot users in your industry to take advantage of their shared knowledge, resources, and tips for success. The Copilot for Microsoft 365 community on the Microsoft Tech Community website is filled with news updates, event details, and discussions related to Copilot for Microsoft 365.
Learning how to use Copilot effectively, developing your prompt engineering and critical thinking skills, and tapping into the knowledge of fellow Copilot users can help you prepare for a new world of work with this AI-powered helper by your side.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.
By Neil du Plessis | Cloud Security Architect, BUI
Copilot for Microsoft 365, the advanced AI assistant embedded in Microsoft 365 apps like PowerPoint and Word, made waves in workplaces worldwide after it was ANNOUNCED IN 2023.
The tool enables people to perform tasks and generate content using natural language commands and is ALREADY CONSIDERED A GAME-CHANGER for productivity and human-computer interaction, even as Microsoft continues to refine its capabilities and features.
So, what can we expect from this innovative technology going forward? Here are four important updates to know about Copilot for Microsoft 365.
On 1 November last year, Microsoft made Copilot for Microsoft 365 available to Microsoft 365 customers on Enterprise plans. Since then, Microsoft has removed the Microsoft 365 prerequisite and minimum-purchase restrictions to expand its Copilot for Microsoft 365 licensing model to include enterprises using Office 365 E3/E5 and small and medium-sized businesses (SMBs).
As of 15 January 2024, Enterprise customers (Office 365 E3, Office 365 E5, Microsoft 365 E3 and Microsoft 365 E5) and Business customers (Microsoft 365 Business Standard and Microsoft 365 Business Premium) can purchase Copilot for Microsoft 365 as an add-on to an existing subscription for $30 per user per month.
Initially, Copilot was only available in English for users based in the United States, Canada, and the United Kingdom. Today, it’s available in 36 regions across the Americas, Europe, Africa, and Asia, and Microsoft is working hard to expand both audience and market reach.
In addition to English, Copilot for Microsoft 365 is supported in Chinese (Simplified), French, German, Italian, Japanese, Portuguese, and Spanish. Microsoft plans to support several more languages over the first half of 2024, including Arabic, Chinese (Traditional), Czech, Danish, Dutch, Finnish, Hebrew, Hungarian, Korean, Norwegian, Polish, Russian, Swedish, Thai, Turkish, and Ukrainian.

Microsoft is enhancing the workplace value of Copilot for Microsoft 365 by adding new features and integrating it with more apps and services – both inside and outside of the Microsoft 365 suite. For example, Copilot works seamlessly with Loop and SharePoint, and is coming soon in Planner, OneNote, and Stream to allow users to access and manage files and tasks through natural language prompts and queries.
Copilot can also connect with third-party apps and services, including Salesforce, Jira, Dynamics 365, Bing Web Search, ServiceNow, and Zendesk, enabling users to perform actions and gather external information without leaving their current app.
Copilot can also leverage the power of the Microsoft Graph and third-party integrated applications like SQL and Confluence to provide users with personalised, contextual suggestions and insights based on their preferences, history, and activity.
Microsoft is committed to improving Copilot for Microsoft 365 so that it consistently produces relevant, high-quality output for users based on their prompts and context. To achieve this, Microsoft has been refining Copilot’s processing and orchestration engine, updating its Large Language Models, and gathering public and partner feedback through early access programmes, preview programmes, and dedicated community forums like the Copilot Feedback Hub, where users can share their observations, suggestions, and experiences with the tool.
These efforts continue to yield results: Copilot’s accuracy and reliability have improved significantly since launch; 70% of early users have reported increased personal productivity; and 77% of early users have said that once they used Copilot, they didn’t want to give it up.
With its expanded licensing model, broader language support, increased integration with apps and services, and improved accuracy and reliability, Copilot for Microsoft 365 is set to become a critical tool for businesses of all sizes.
As Microsoft further refines Copilot’s capabilities and features, we can expect this AI-powered assistant to revolutionise organisations everywhere by empowering people to do more with their favourite Microsoft 365 apps every day.
BUI Cloud Security Architect Neil du Plessis is a certified CISSP and Microsoft Cybersecurity Expert specialising in holistic, cloud-powered defences for modern workplaces.
Wondering if Copilot for Microsoft 365 is right for your organisation? Join the BUI team for an interactive workshop and we’ll assess your Copilot for Microsoft 365 readiness and define a road map for your adoption journey. The workshop is conducted virtually, and is suitable for senior business development managers, line-of-business leaders, managers, technical decision-makers, and end-users. Register your interest by completing this digital form and we’ll contact you directly.